Technology
How does it work?
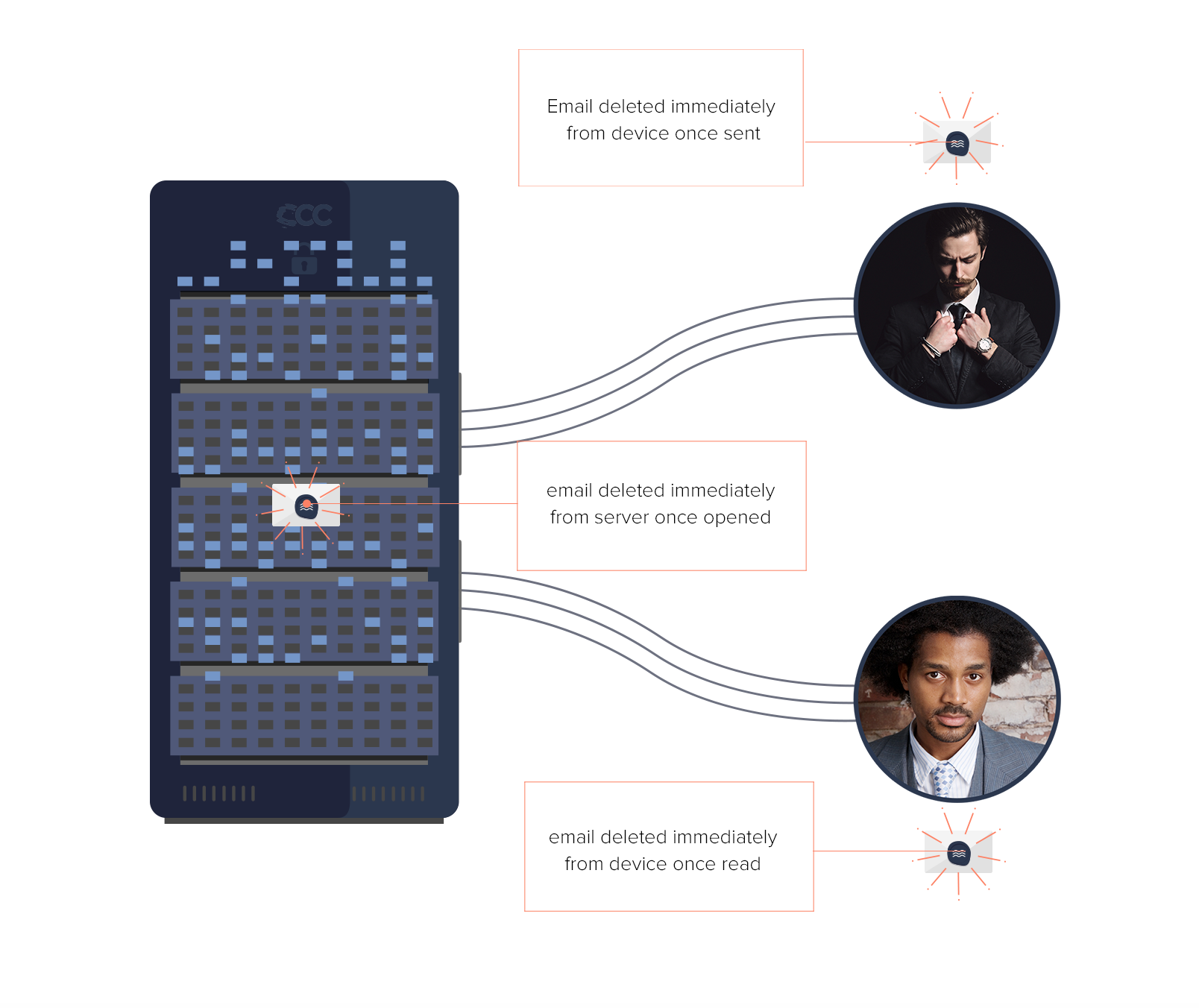
Every Ccc: message and associated attachments are encrypted end-to-end and deleted immediately once read. Even if we wanted to read, share or restore the message... we can't.
Technology
How does it work?
Every Ccc: message and associated attachments are encrypted end-to-end and deleted immediately once read. Even if we wanted to read, share or restore the message... we can't.

Our Promise To You
Our Promise to You
Our Promise To You
Our Promise to You
Premium protection
Each Ccc: message is encrypted end-to-end and self-destructs without a trace. No data is ever kept or logged on our servers and no content is ever saved on a user's device or cached. Messages are decrypted on the sender's device once sent, and on the receiver's device once read.
Minimal data retention
Confidential CC retains the minimal amount of information about our customers' activities as possible. A login technology called oAUTH2 is utilized when possible, which provides a unique and secure token i.d. to guarantee your login method secure and private. In turn, your user name and password are never stored and always secure.
Hardware
The security of our servers, networks, and equipment is equally as important as data security. Confidential CC uses best-in-class security technologies to protect the hardware that transmits your messages. Since we believe these are only your business, we would never share this information with anyone.